In a previous tutorial I showed installation of Clonezilla Server Edition on Ubuntu using my own Bash script. We configured PXE (Pre eXecution Environment)) password for clients so when the clients booted a password had to be entered to startup. This tutorial explains two different ways how to get and crack the PXE boot password.
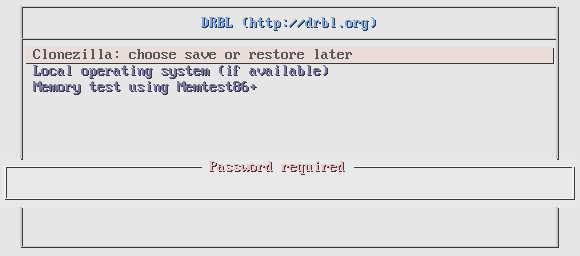
Picture 1 - Client Requires to Enter PXE Password During Startup
First, we should mention some facts. The PXE client password is stored in plain text in a configuration file /etc/drbl/drblpush.conf. The password is secretpassword and it can be found in a dictionary rockyout.txt.
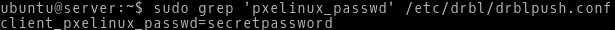
Picture 2 - Plain Text PXE Client Boot Password
The same PXE client password is stored as a hash in a file /tftpboot/nbi_img/prelinux.cfg/default.
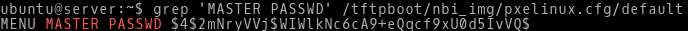
Picture 3 - PXE Client Boot SHA-1 Base64 Encoded Salted Hash
The hash is created by utility /usr/sbin/sha1pass on DRBL server. It is a Perl script which takes two arguments from STDIN - a password and salt and it creates SHA-1 base64 salted hash.
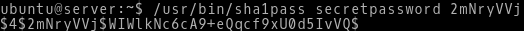
Picture 4 - Perl Script fo Generating Hash from Password and Salt
Explanation:
- $4$ - SHA-1 base64 encoded salted hash
- 2mNryVVj - salt
- WIWlkNc6cA9+eQqcf9xU0d5IvVQ - hash
They are several methods how to obtain PXE boot password. The first method is based on downloading a file /tftpboot/nbi_img/prelinux.cfg/default which contains a hash from TFTP server and cracking the hash with a tool such as john or hashcat. This method is not very practical so use it only if you want to practice your hacking skills. Moreover if a dictionary does not contain a password, your attempt very likely end up without success. The second method is fast and reliable and relies on mounting remote shared NFS directory which contains a file with a plain-text password PXE boot password.
1. Cracking Hash
Let's say we have Linux with installed DRBL server with TFTP and DHCP server running on IP address 192.168.112.200/24. A client obtains its IP address 192.168.122.8/24 from DHCP server together together with info about a boot file pxelinux.0. The client downloads the file pxelinux.0 from a TFTP server from a root directory/tftpboot/nbi_img/. Client also downloads files ldlinux.c32, pxelinux.cfg/default from TFTP server. As we have mentioned before, the file /tftpboot/nbi_img/prelinux.cfg/default contains the hashed password. The hash is shown on the picture 5. Captured pcap traffic between DRBL server 192.168.112.200 and client 192.168.112.8 can be downloaded here.
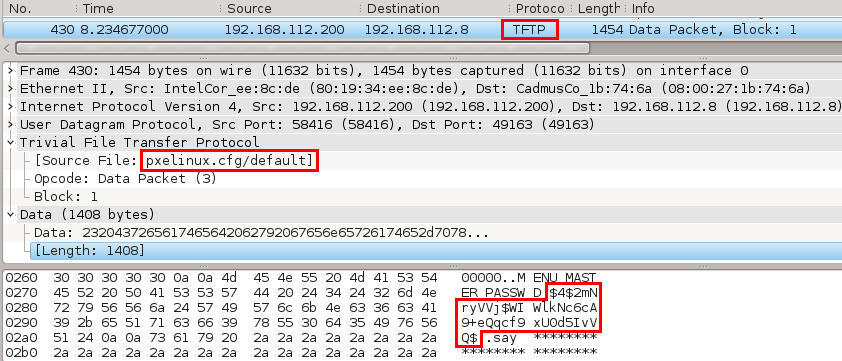
Picture 5 - Captured SHA-1 Base64 Encoded Salted Password Hash
I have created a BASH script get_sha1.sh that downloads a file/tftpboot/nbi_img/prelinux.cfg/default from TFTP server and extracts SHA-1 base64 salted hash from the file together with the salt. It also converts the hash from SHA-1 base64 encoded format to SHA-1 hexa encoded format and put it to format recognized by hashcat - sha1($salt.$pass):
5885a590d73a700f7e790a9c7fdc54d1de48bd54:2mNryVVj

Picture 6 - Script for Converting Between Salted SHA-1 Base64 and SHA-1 Hexa Hashes
1.1 Hashcat Instllation and Cracking
$ wget https://hashcat.net/files_legacy/hashcat-2.00.7z
$ mkdir hashcat && mv hashcat-2.00.7z hashcat && cd hashcat/
$ 7z e hashcat-2.00.7z
Download dictionary:
$ wget http://scrapmaker.com/data/wordlists/dictionaries/rockyou.txt
Let's say we have our hash stored in a file hash_decoded.txt.
$ ./hashcat-cli64.bin -m 120 hash_decoded.txt rockyou.txt
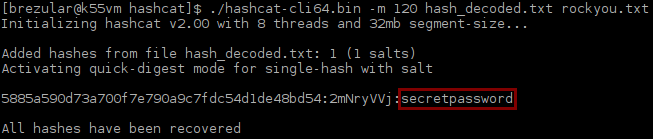
Picture 7 - Cracking SHA-1 Salted Hash with Hascat
2. Getting Plain Text Password
In fact, we do not need to download and crack a salted SHA-1 base64 encoded password hash. We can mount a shared remote NFS directory on DRBL server to a local directory and extract a plain text password stored in a file drblpush.conf.
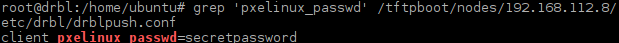
Picture 8 - Plain Text PXE Boot Password Stored in Drblpush.conf for Client 192.168.112.8
I have written a Bash script get_plain_pass.sh which mounts a remote NFS directory and extract a plain text password. The script takes an IP address of DRBL/Clonezilla server as an argument.
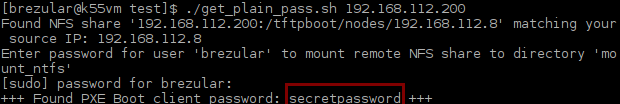
Picture 9 - Getting Plain Text PXE Boot Password Using NFS Share
End.